
Powerful data privacy and enhanced productivity for a leading KPO service provider
One of India’s largest BPO/KPO organizations needed to ensure the security of the highly sensitive healthcare data under their management.
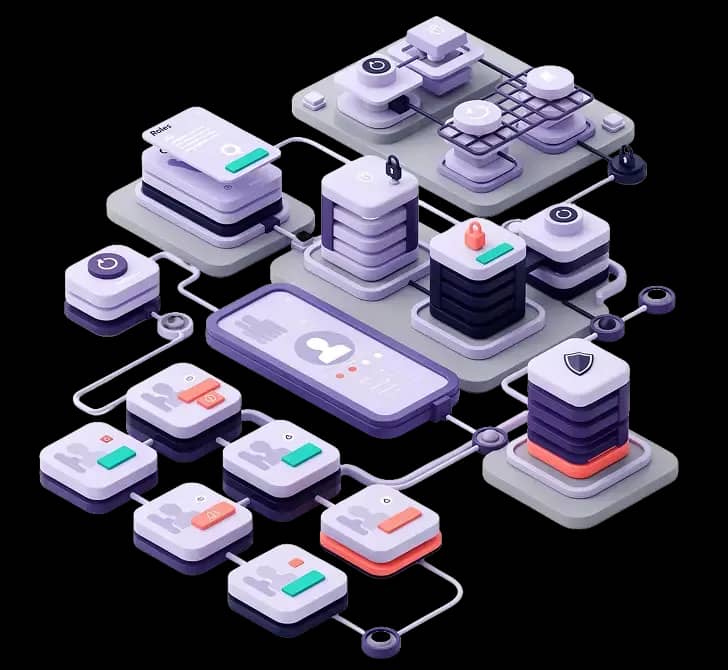
Identity Governance & Administration (IGA) is a comprehensive approach to managing user identities and access rights across your organization to provide secure, automated control over who has access to what, when, and why.
It enables organizations to enforce consistent access policies, maintain compliance with regulations such as GDPR, HIPAA, and SOX, and reduce security risks through automated user lifecycle management, role-based access control, and continuous access reviews.
Automate the complete user journey from initial provisioning during employee onboarding through ongoing role and access modifications, to comprehensive, one-click deprovisioning at employee exit. Eliminate manual processes, reduce operational errors, and strengthen your security framework.
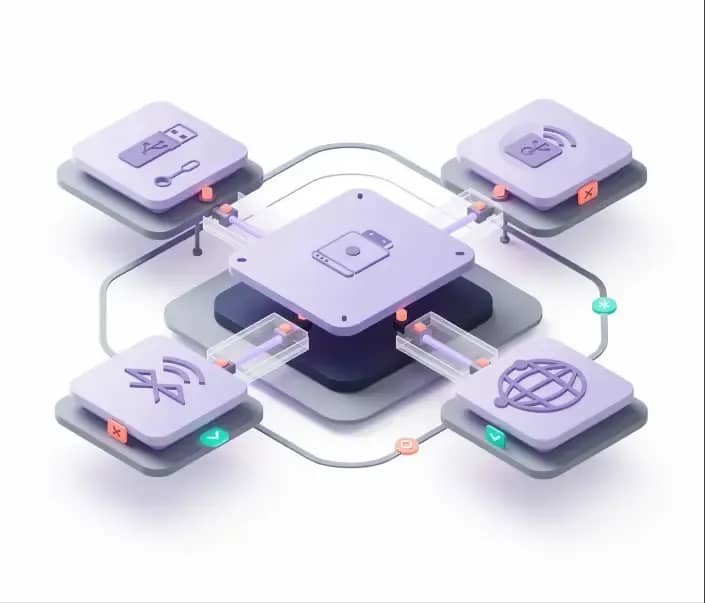
Implement smart role-based access control that ensures users receive the appropriate permissions based on their organizational role. With Akku’s Segregation of Duties (SoD) Rules Engine, you can define rules to prevent overlapping roles, and detect and mitigate violations, helping you maintain high security and compliance standards across your organization.

Enable faster access requests with smarter approvals while maintaining security governance. Streamline how users request additional access beyond their standardized group permissions, enforce approval workflows, and conduct automated access reviews to ensure ongoing compliance and eliminate orphan accounts across your infrastructure.

Loading...